Oomnitza recognized by Gartner® in new Market Guide for Hardware Asset Management Tools



Run IT with Data
You Can Trust.
Automate IT workflows with confidence using accurate, comprehensive and actionable technology data to enhance compliance, security, productivity and cost efficiency.

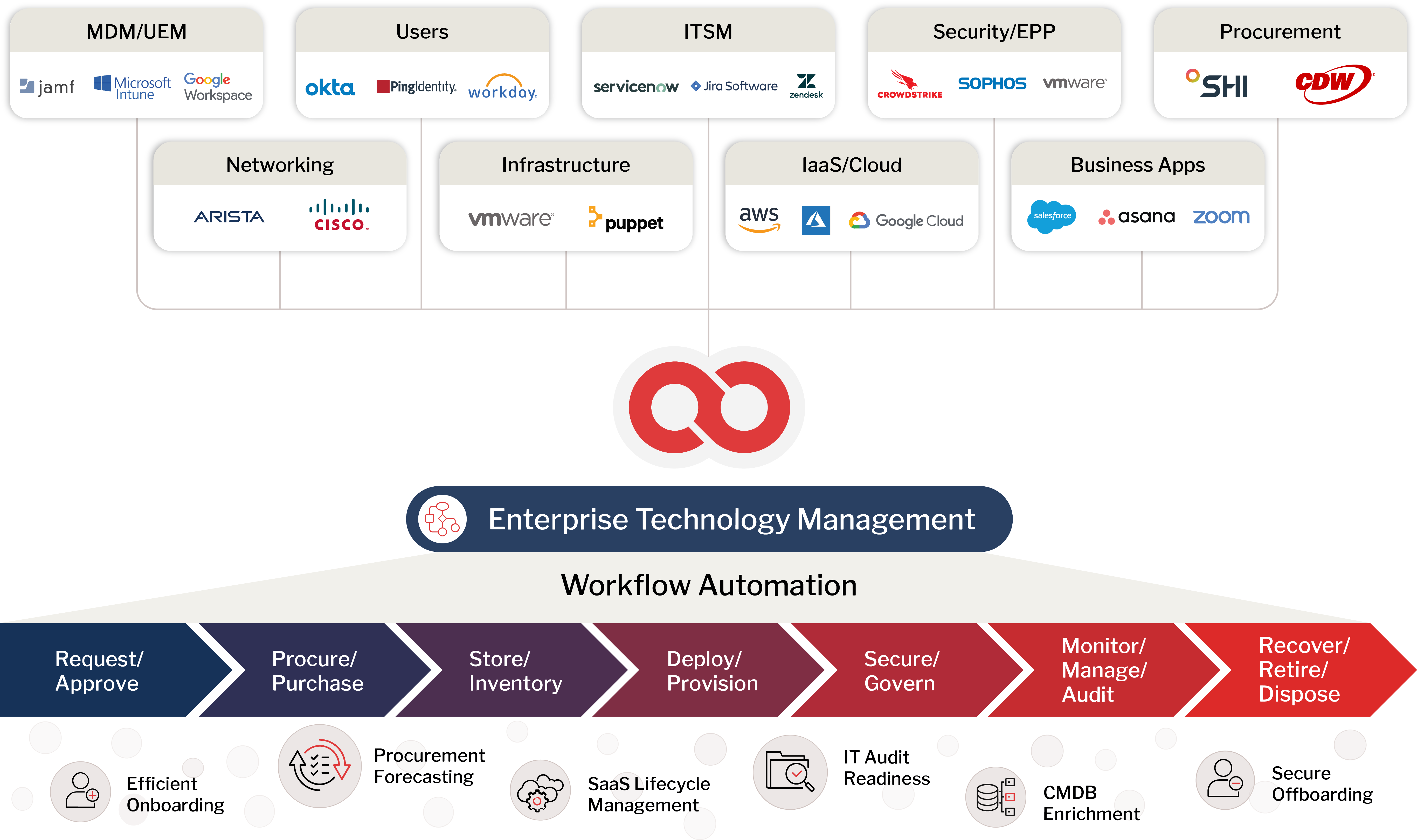
Oomnitza provides an Enterprise Technology Management (ETM) solution that empowers IT organizations to scale by orchestrating and automating processes across siloed technologies.
"Technology is now considered a critical resource to the enterprise. In order to manage this technology, it requires its own system for key business process. Enterprise Technology Management is the single system of record for technology. Just like CRM is for customers. HCM is for employees. ERP is for financials. It’s time for CIOs to have their own enterprise application."
Arthur Lozinski
Oomnitza CEO and Co-Founder
Take Control of your Technology Ecosystem
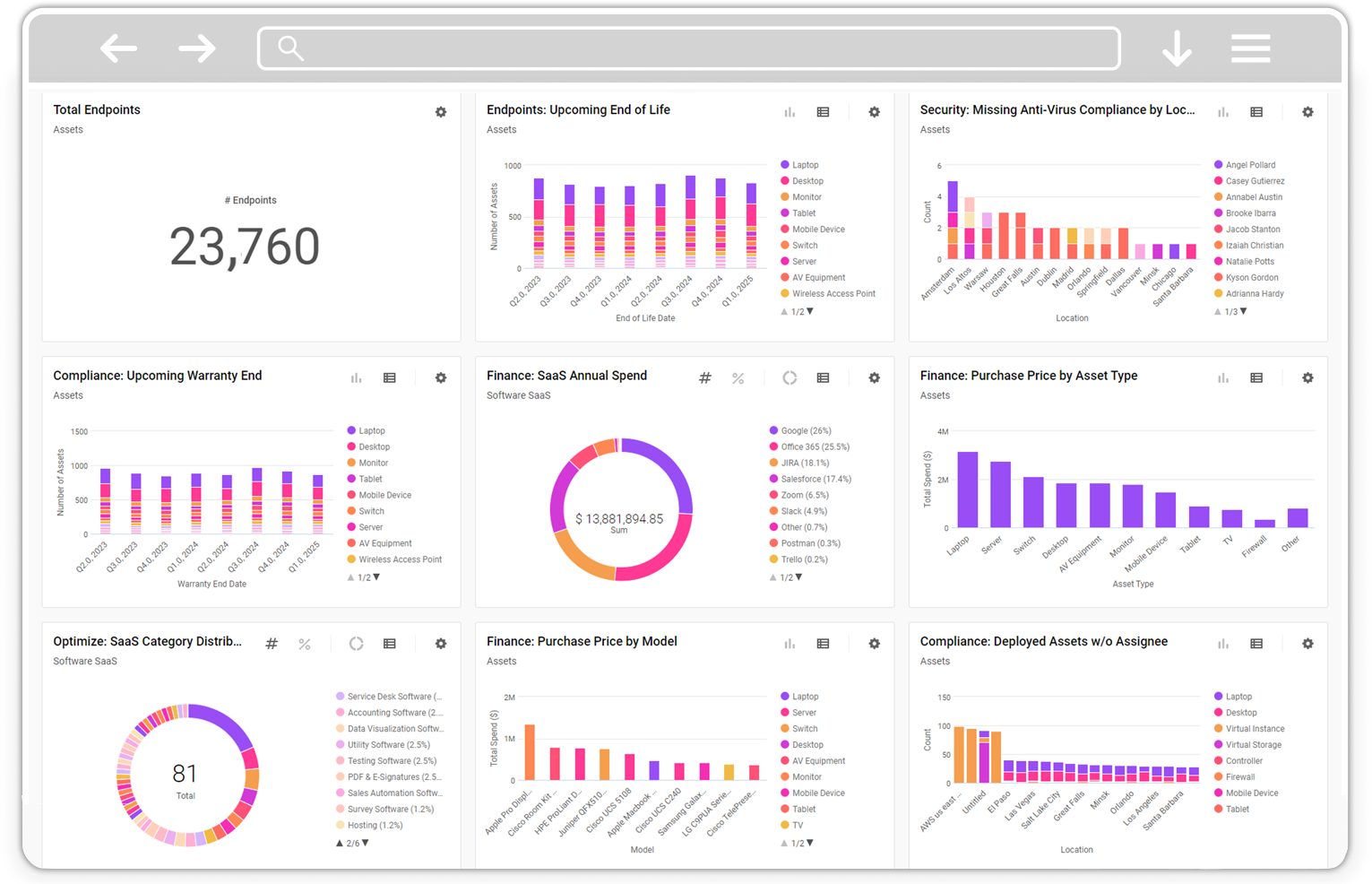
Enterprise Technology Management (ETM) solutions integrate with your existing IT, security and business systems to aggregate and correlate multi-source data for better data hygiene and accurate inventory controls. Leverage this technology inventory to automate workflows for asset lifecycle management, improve IT efficiency, and reduce security and compliance risk. Discover Oomnitza and eliminate manual tasks, reduce tickets and optimize IT spend.

Why IT Teams Choose Oomnitza
Unified and accurate technology inventory and controls
reduction in time preparing
for IT audits
increase in asset reclamation during offboarding
improvement in refresh forecasting accuracy
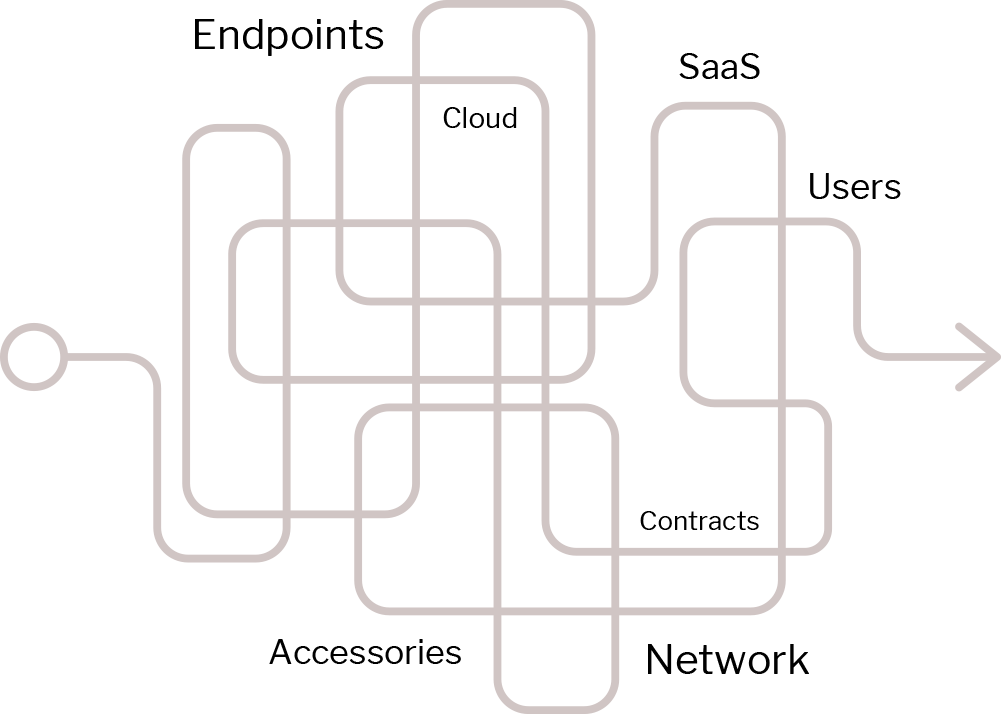

Accurate Inventory Controls
Finally, trust your technology data.
- Overcome siloed tools and fragmented data
- Gain visibility over your entire tech environment
- Leverage existing IT, security & business systems
- Aggregate and correlate multi-source data
- Enrich CMDB, ITSM and other existing tools
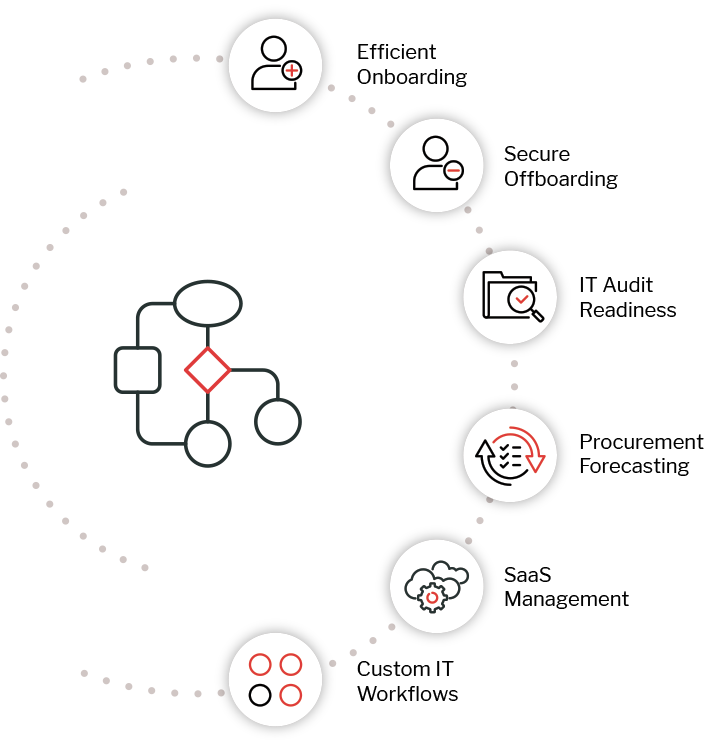
Workflow Automation
Automate smarter, not harder.
- Automate with accurate technology data
- Eliminate repetitive, error-prone, manual tasks
- Leverage pre-packaged low-code workflows
- No custom, proprietary, in-house development
- Automate millions of workflows daily

Harness the Tools You Have to Power the Control You Need
Integrate with 160+ systems and orchestrate actions with 1500+ pre-built connectors supported by Oomnitza.
Automation Versatility for Accelerated Results
Related Resources



Experience Oomnitza Up Close
Schedule a demo with one of our Enterprise
Technology Management experts today.