Many companies face the challenge of maintaining visibility over their technology assets, including endpoints, applications, and infrastructure, to meet compliance and audit requirements. With the explosion in technology utilized by modern businesses over the past decade, keeping track of a company’s assets has become ever more challenging.
To address this issue, the Oomnitza Enterprise Technology Management (ETM) solution enables the automation of IT processes with standardized Workflow applications run on a Modern Technology Asset Management foundation. One such ETM Workflow Application, IT Audit Readiness and Compliance, enables comprehensive asset visibility into a company's entire technology asset portfolio, enabled through Modern Technology Asset Management, greatly enhancing a company’s compliance and audit readiness.
The need for comprehensive asset visibility
Regardless of the IT governance and cybersecurity framework followed by a business, inventory control is a critical aspect. For example, the Center for Internet Security (CIS) Critical Security Control 1 emphasizes the importance of Inventory and Control of Enterprise Assets. Lack of visibility into the physical locations of endpoints like laptops and their access permissions creates a significant attack surface vulnerability. To put this risk into perspective, according to Security Boulevard, 86 percent of IT practitioners report that someone in their organization has had a laptop lost or stolen, with 56 percent of them reporting that this resulted in data breach.
Inadequate asset visibility not only leads to compliance violations and audit failures but also hinders operational efficiency, as IT scrambles to manually update logs when an audit is announced. That said, incomplete documentation and audit trails can exacerbate the challenge of passing audits, as auditors rely on comprehensive records for asset transactions. In addition, difficulty in locating assets when needed can cause delays, downtime, and suboptimal resource utilization. It may also lead to redundant asset acquisitions, inefficient maintenance, and challenges in retiring outdated assets.
Legacy ITAM Approach Limitations
To help mitigate these risks, many companies turn to some form of asset tracking and inventory management systems, such as traditional IT Asset Management (ITAM) solutions. These solutions often rely on a centralized asset database, such as a configuration management database (CMDB). However, CMDBs face significant challenges in data quality and incompleteness. In fact, Gartner reports that a mere 25% of organizations derive significant value from their CMDBs.
Inconsistent data quality
The effectiveness of a CMDB relies heavily on the quality of its data sources. Two prevalent approaches include manual entry and authenticated active scanning. Manual entry is susceptible to errors, with 60% of data manually entered by employees inaccurate by one estimate. Meanwhile, authenticated active scans can provide reasonably accurate information for managed IT devices, but they often misidentify hardware components.
In complete asset inventory
Many CMDBs incorporate a discovery module capable of conducting authenticated scans on known assets (such as virtual machines, servers, and storage systems) and automatically updating records. While this approach adequately addresses managed IT assets, it falls short in accounting for the unknowns, including unmanaged assets, as well as IoT and OT devices.
Indeed, security teams often encounter compromised assets that do not appear in their CMDBs, resulting in a lack of vital context and details required for swift action during critical security incidents. In today's landscape, characterized by hybrid or fully remote workforces, the need for a comprehensive view of all assets—both managed and unmanaged—has never been more critical for effective security and management. Relying solely on CMDB-based discovery or passive scanning proves insufficient as it overlooks devices not connected to the corporate network. To attain comprehensive asset visibility, a holistic approach is indispensable, combining unauthenticated active scans with API integrations.
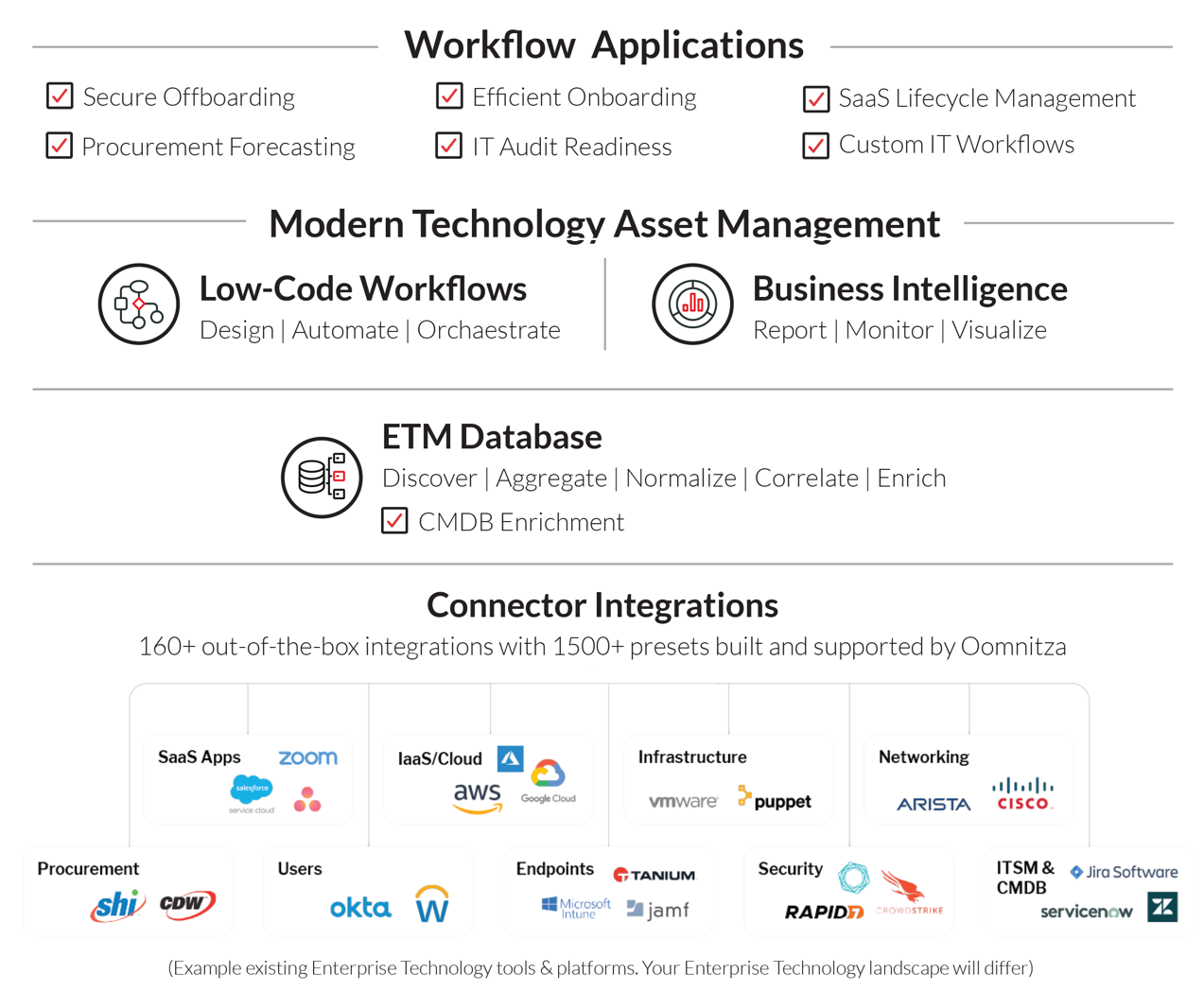
Figure 1: Oomnitza Enterprise Technology Management (ETM) architecture
The Modern Technology Asset Management and ETM Database Approach
To address these obstacles, Oomnitza ETM offers standardized Workflow Applications built upon a Modern Technology Asset Management (see figure 1). Unlike traditional IT Asset Management solutions, which primarily focus on asset counting and tracking, Modern Technology Asset Management goes beyond these functionalities.
For example, while some systems with agents can offer partial asset visibility, Oomnitza Modern Technology Asset Management distinguishes itself as an agentless solution that seamlessly integrates with all management tool datasets via its built-in connector integrations. This multi-source visibility empowers IT to efficiently pinpoint compliance gaps, such as endpoints operating with outdated patches or lacking essential security software. The identified issues can then be promptly reported to IT and security teams, facilitating remediation actions.
To accomplish this, Modern Technology Asset Management by Oomnitza incorporates essential components that enable you to automate workflows for end-to-end asset lifecycle management across all of your technology assets – including hardware, software/SaaS, virtual and cloud assets. This provides unparalleled insight into their ownership, state, location, security posture and lifecycle context at all times.
These foundational components include:
- 160+ Connector Integrations built and supported by Oomnitza that
- Connect to an ETM Database that continuously provides data accuracy across your entire technology asset portfolio
- Business Intelligence to report on your technology assets
- Low-Code Workflows that turn information into action
For a review of these components, read my Oomnitza Modern Technology Asset Management article. You can also download the Oomnitza Solution Overview for an even more detailed description.
ETM Workflow Applications, like IT Audit Readiness and Compliances, leverage the ETM database and standardized low-code workflows to automate audit readiness and compliance validation, reducing audit delays, gaps, costs, and penalties.
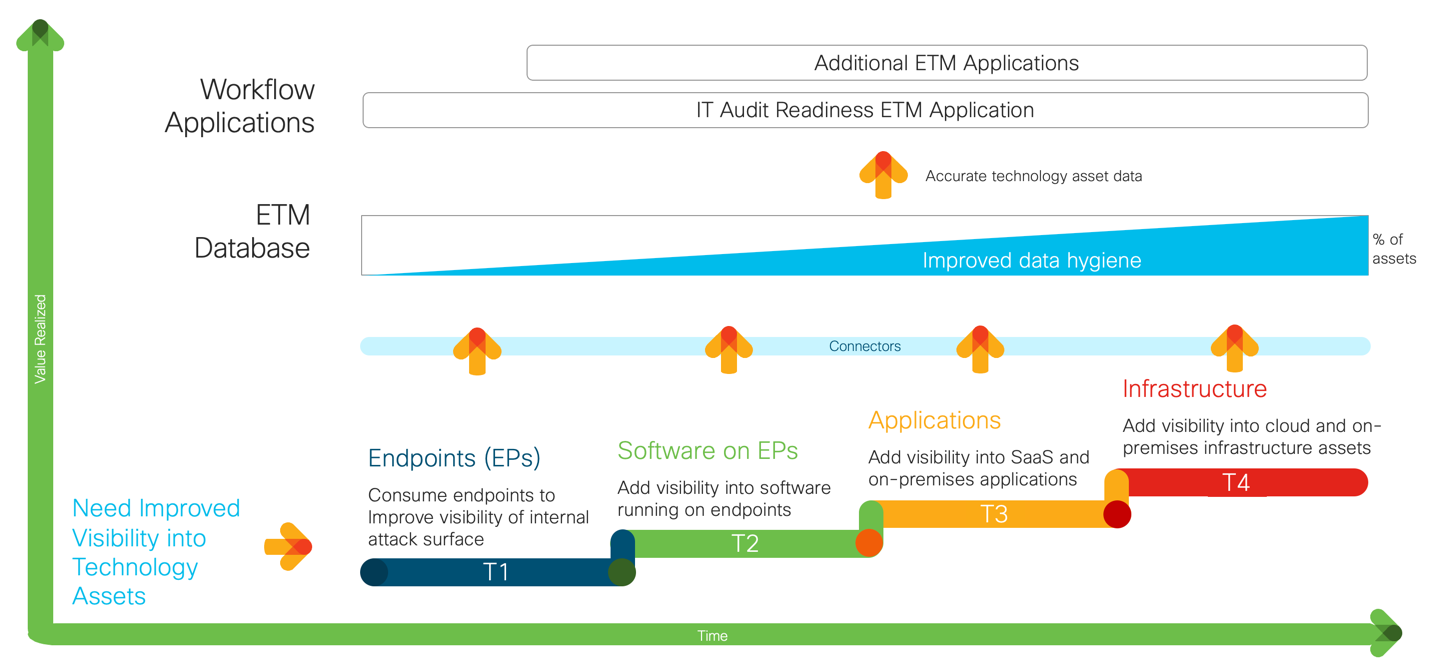
Figure 2: Example ETM Customer Journey
Typical ETM Customer Journey
As shown in Figure 2, companies often start their ETM and Modern Technology Asset Management journey with Oomnitza by connecting their endpoints first, gradually expanding to adding endpoint software, applications, and infrastructure. This incremental approach improves asset visibility and enhances data integrity throughout the organization. As companies witness the benefits, they often further expand their ETM deployment by incorporating additional ETM Workflow Applications to optimize asset management capabilities.
In conclusion, embracing the Modern ITAM approach of deploying an IT Audit Readiness and Compliance ETM Workflow Application offers companies a better way to achieve comprehensive asset visibility, meet compliance and audit requirements, and streamline IT processes efficiently.
Interested in learning more?
- Download the Oomnitza Solution Overview.
- Check out the self-paced, click-through product tour.
- Book a demo and let Oomnitza provide a product demo.
