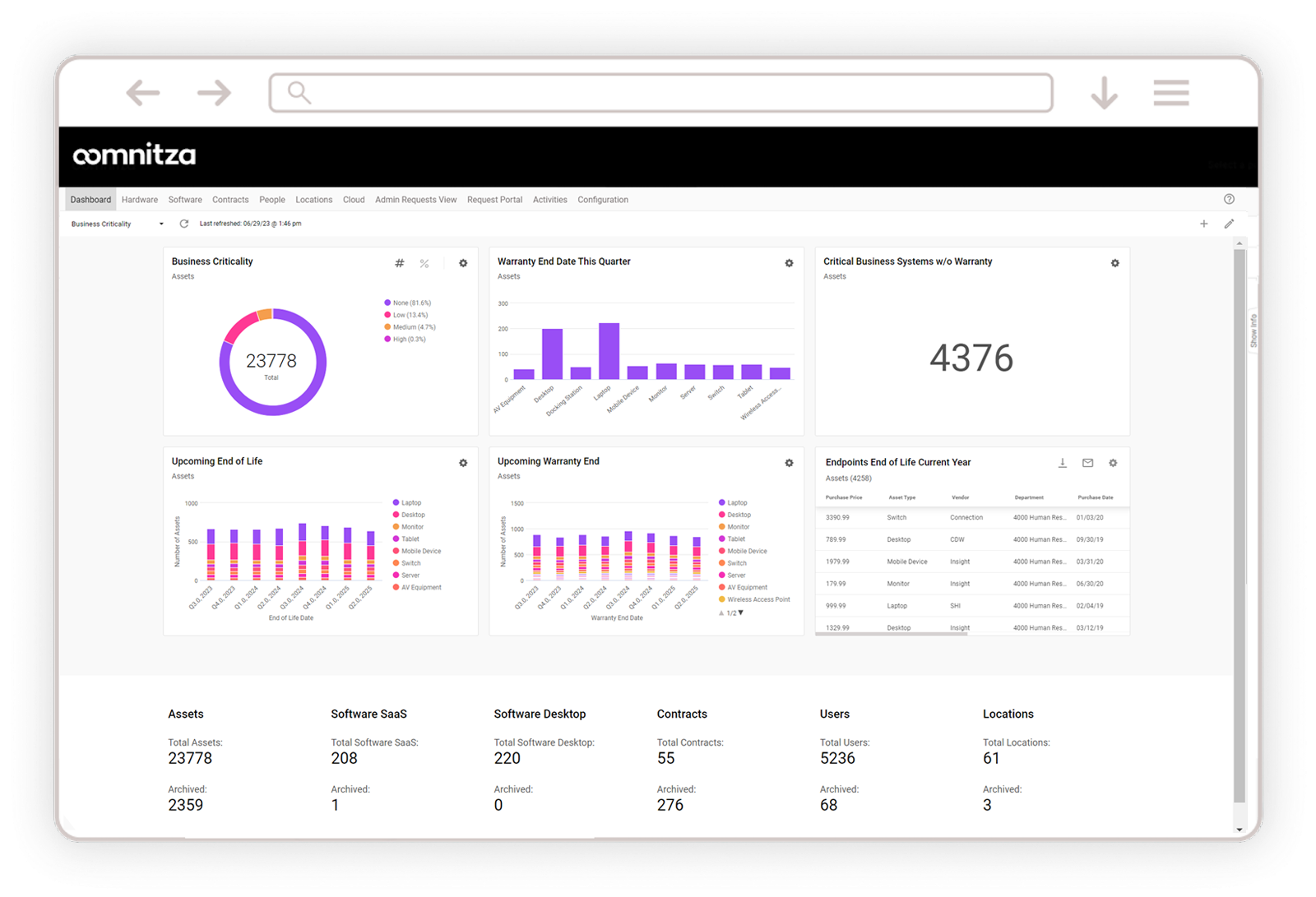
Technology Inventory Controls
Accurate inventory management is the cornerstone of most IT compliance mandates. Unfortunately, modern enterprise environments, characterized by hybrid and remote work, cloud infrastructure and applications, and mobile technologies, have added layers of complexity to maintaining accurate inventory controls and good technology data hygiene.
Data Silos
Enterprises use 11+ tools/databases for audits and 40% have accuracy issues due to conflicting data from different tools.1
Data Accuracy
46% of organizations experienced considerable increases in audit delays and costs due to inaccurate asset data.2
Data Consolidation
51% of IT professionals say that data synchronization across systems and applications is a significant challenge.1
Technology Inventory Controls with Oomnitza
achieved unified and centralized technology inventory
reduction in time preparing for technology audits
decrease in ticket volume for technology asset management
improved service desk response time with better asset context
Oomnitza’s Enterprise Technology Management (ETM) solution integrates with your existing IT, security and business systems to discover and aggregate multi-source data and deliver a unified technology inventory across endpoints, software/SaaS, cloud, networking, accessories and other digital assets. It serves as a central hub to manage the lifecycle of your technology assets using low-code/no-code workflows to automate processes such as employee onboarding and offboarding, IT audit readiness, procurement forecasting and more.
Manage Technology Lifecycles from Purchase to End-of-Life
Traditional asset management focuses on counting and tracking assets for inventory and accounting purposes. Often, IT teams resort to managing the lifecycle of their technology assets painstakingly via manual execution of service tickets.
Enterprise Technology Management (ETM) enables you to automate workflows for end-to-end technology lifecycle management across hardware, software/SaaS, virtual and cloud assets so you have unparalleled insight into their ownership, state, location, security posture and lifecycle context at all times.
- Improve procurement forecasting, purchasing schedules and IT budgeting accuracy
- Provision/deprovision assets for onboarding, offboarding, tech refresh, internal moves etc.
- Monitor utilization and compliance, remediate security gaps and be audit-ready at all times
- Track and document EOL and disposal, identify redundancies, rightsize renewals and refreshes
Power Lifecycle Workflows with Enterprise Technology Management
The Oomnitza Advantage
Discover
and Aggregate
We integrate with 160+ systems without installing new agents to discover and aggregate asset data from your existing technology management tools and give you a single, unified view of your enterprise technology landscape.
Correlate
and Enrich
We enable you to reconcile multi-source asset data and remove redundancies and inconsistencies between disparate systems. Then enrich the data with information from additional data sources so you’re always audit ready.
Automate
Lifecycle Workflows
Armed with accurate, high-fidelity asset data, we enable you to confidently automate your IT processes using low-code workflows, such as on/offboarding, IT audit readiness, SaaS management, procurement forecasting and more.
Share
Context
We enable you to share reliable asset data from this system-of-record with your other systems such as CMDB, ITSM, procurement and financial management, HRIS and more, to enhance their ROI and improve decision making.
Explore Additional Use Cases
Onboarding
Automate employee onboarding to improve IT efficiency and increase employee productivity, engagement and job satisfaction.
Offboarding
Streamline and strengthen every step of the offboarding process. Perform actions and set up automated workflows within a single platform.
Readiness
Automate audit readiness and compliance validation to increase risk mitigation efficacy and reduce audit delays, gaps, costs and penalties.
Forecasting
Automate lifecycle management processes for all technology assets to improve IT budgeting, forecasting and procurement.
Management
Automate SaaS lifecycle processes to improve utilization, mitigate cyber risk and eliminate wasteful spend.
Conductor
Orchestrate across your existing infrastructure tools to automate key business processes, increase IT efficiency and improve decision making.
& Hygiene
Continuously achieve data accuracy across your entire technology asset-portfolio.
Related Resources



Experience Oomnitza Up Close
Schedule a demo with one of our Enterprise
Technology Management experts today.